So, you're probably wondering how to use RemoteIoT behind a firewall on Windows, right? Well, let me tell you, it's like trying to sneak into a party where the bouncer is extra strict. But don’t worry, we’ve got your back. Firewalls can be tricky, but with the right steps, you can set up RemoteIoT without breaking a sweat. Whether you're a tech enthusiast or just someone looking to connect devices securely, this guide will help you navigate through the maze of firewalls and networks.
RemoteIoT is all about connecting devices remotely, and it’s become super popular these days. From smart homes to industrial automation, the possibilities are endless. But here’s the catch – most corporate networks and even home routers come equipped with firewalls that block unauthorized access. So, if you want to use RemoteIoT, you gotta know how to play by the rules while bending them just enough to get things done.
This article is your ultimate cheat sheet for setting up RemoteIoT behind a firewall on Windows. We’ll cover everything from understanding firewalls to configuring port forwarding and even troubleshooting common issues. By the time you finish reading, you’ll feel like a pro who can tackle any network challenge thrown your way. Ready to dive in? Let’s go!
Read also:Securely Connect Remote Iot P2p Raspberry Pi Download Windows Free A Comprehensive Guide
Table of Contents
- Understanding Firewalls and Their Role
- What is RemoteIoT and Why Does It Matter?
- Configuring Your Firewall for RemoteIoT
- Setting Up Port Forwarding on Windows
- Using VPNs to Bypass Firewalls
- Exploring Third-Party Tools for RemoteIoT
- Security Best Practices for RemoteIoT
- Troubleshooting Common Issues
- Optimizing Performance Behind Firewalls
- Conclusion: Wrapping It All Up
Understanding Firewalls and Their Role
Before we jump into the nitty-gritty of RemoteIoT, let’s take a moment to understand what firewalls are and why they exist. Think of a firewall as a security guard standing at the entrance of your network. Its job is to monitor incoming and outgoing traffic, ensuring that only authorized connections pass through. While firewalls are essential for protecting your system from cyber threats, they can sometimes block legitimate applications like RemoteIoT.
Firewalls come in different flavors – hardware firewalls, software firewalls, and cloud-based firewalls. For most home users, the built-in Windows Firewall is sufficient, but businesses often use more advanced solutions. Understanding your firewall’s configuration is key to successfully setting up RemoteIoT.
Here’s a quick rundown of how firewalls work:
- They filter traffic based on predefined rules.
- They can block or allow specific IP addresses, ports, and protocols.
- They log all network activity for monitoring purposes.
Why Firewalls Matter in RemoteIoT
When you’re working with RemoteIoT, firewalls can either be your best friend or your worst enemy. On one hand, they protect your devices from unauthorized access. On the other hand, they can prevent RemoteIoT from establishing a connection. The trick is to configure your firewall in a way that allows RemoteIoT to function while still maintaining security.
What is RemoteIoT and Why Does It Matter?
Now that we’ve covered the basics of firewalls, let’s talk about RemoteIoT. Simply put, RemoteIoT is a technology that allows you to control and monitor IoT devices from anywhere in the world. Whether you’re managing a fleet of sensors or controlling smart appliances, RemoteIoT makes it possible to do so without being physically present.
Here are some scenarios where RemoteIoT shines:
Read also:Mindy Mccready Sons Today 2024 Where Are They Now
- Monitoring environmental conditions in remote locations.
- Controlling industrial equipment from a central dashboard.
- Managing home automation systems while you’re on vacation.
But here’s the thing – to make RemoteIoT work behind a firewall, you need to understand how it communicates. Most RemoteIoT solutions rely on specific ports and protocols, which can be blocked by firewalls. That’s why proper configuration is crucial.
Configuring Your Firewall for RemoteIoT
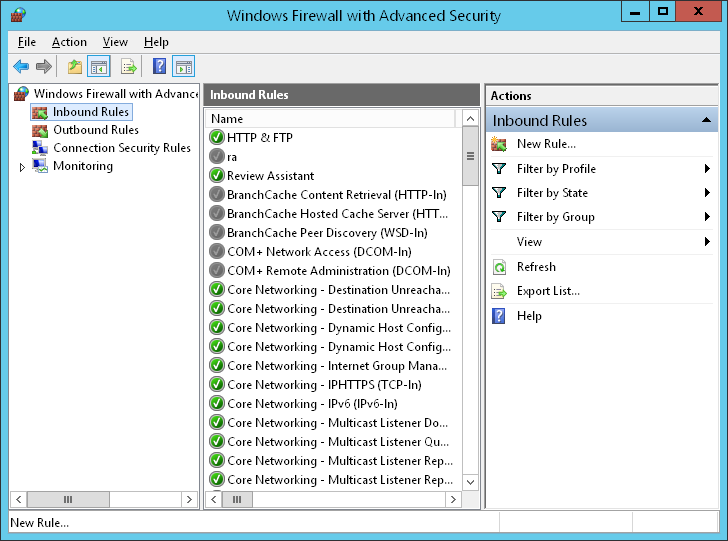
Configuring your firewall might sound intimidating, but it’s actually pretty straightforward. The first step is to identify the ports and protocols that RemoteIoT uses. Once you know this, you can create rules in your firewall to allow those connections.
For example, if RemoteIoT uses TCP port 8080, you can create an inbound rule in the Windows Firewall to allow traffic on that port. Here’s how you do it:
- Open the Windows Firewall with Advanced Security.
- Click on "Inbound Rules" and select "New Rule."
- Choose "Port" as the rule type and specify the port number (e.g., 8080).
- Set the action to "Allow the connection" and apply it to all network profiles.
Don’t forget to test your setup after making these changes. You can use tools like telnet or netstat to verify that the port is open and accessible.
Common Firewall Settings for RemoteIoT
Every RemoteIoT solution is different, so the ports and protocols may vary. However, here are some common settings you might encounter:
- HTTP/HTTPS: Ports 80 and 443
- MQTT: Port 1883
- WebSocket: Port 8080
Make sure to consult the documentation for your specific RemoteIoT platform to get the exact details.
Setting Up Port Forwarding on Windows
Port forwarding is another essential step when using RemoteIoT behind a firewall. It allows you to direct incoming traffic from the internet to a specific device on your local network. Without port forwarding, RemoteIoT won’t be able to connect to your devices from outside the network.
Here’s how you can set up port forwarding on a typical router:
- Log in to your router’s admin interface using its IP address (usually 192.168.1.1).
- Find the "Port Forwarding" or "NAT" section in the settings menu.
- Add a new rule and specify the external port, internal IP address, and internal port.
- Save the changes and restart the router if necessary.
Remember to assign a static IP address to the device you’re forwarding traffic to. This ensures that the port forwarding rule always points to the correct device.
Tips for Effective Port Forwarding
Port forwarding can sometimes be finicky, so here are a few tips to help you troubleshoot:
- Double-check the port numbers and IP addresses in your forwarding rules.
- Test the connection using an external tool like canyouseeme.org.
- Disable any conflicting firewall rules that might block the forwarded traffic.
Using VPNs to Bypass Firewalls
If configuring firewalls and port forwarding seems too complicated, you might want to consider using a VPN. A Virtual Private Network creates a secure tunnel between your device and the RemoteIoT server, bypassing any firewalls in the process.
Here’s how a VPN can help:
- It encrypts all traffic, making it invisible to firewalls.
- It allows you to connect to RemoteIoT from anywhere in the world.
- It simplifies the setup process by eliminating the need for port forwarding.
There are plenty of VPN services available, both free and paid. Just make sure to choose one that supports the protocols and ports required by RemoteIoT.
Choosing the Right VPN for RemoteIoT
Not all VPNs are created equal, so it’s important to select one that meets your needs. Here are a few factors to consider:
- Speed: Look for a VPN with low latency and high bandwidth.
- Security: Ensure the VPN uses strong encryption and has a no-logs policy.
- Compatibility: Check if the VPN supports the platforms and devices you use.
Exploring Third-Party Tools for RemoteIoT
In addition to firewalls and VPNs, there are several third-party tools that can help you use RemoteIoT behind a firewall. These tools often provide additional features like device management, data analytics, and automation.
Some popular options include:
- ThingsBoard: An open-source IoT platform with advanced analytics capabilities.
- Node-RED: A flow-based programming tool for connecting IoT devices.
- Losant: A cloud-based IoT platform with drag-and-drop interface.
These tools can simplify the setup process and enhance the functionality of your RemoteIoT solution. Just make sure to evaluate them carefully before committing to one.
Advantages of Using Third-Party Tools
Third-party tools offer several advantages over manual configurations:
- They reduce the complexity of setting up RemoteIoT.
- They provide additional features that enhance the user experience.
- They often come with support and documentation to help you troubleshoot issues.
Security Best Practices for RemoteIoT
Security should always be a top priority when working with RemoteIoT. Firewalls and VPNs are great, but they’re not enough on their own. Here are some best practices to keep your devices and data safe:
- Use strong passwords and enable two-factor authentication.
- Regularly update your firmware and software to patch vulnerabilities.
- Monitor network activity for any suspicious behavior.
Remember, security is an ongoing process. Stay vigilant and educate yourself on the latest threats and trends in the IoT space.
Troubleshooting Common Issues
Even with the best preparation, things can still go wrong. Here are some common issues you might encounter when using RemoteIoT behind a firewall, along with solutions:
- Connection Refused: Check your firewall rules and ensure the correct ports are open.
- Timeout Errors: Verify your port forwarding settings and test the connection externally.
- Authentication Failed: Double-check your login credentials and reset them if necessary.
If all else fails, consult the documentation for your RemoteIoT platform or reach out to their support team for assistance.
Optimizing Performance Behind Firewalls
Finally, let’s talk about performance optimization. Firewalls can sometimes slow down your connections, especially if they’re configured incorrectly. Here are a few tips to keep your RemoteIoT setup running smoothly:
- Use compression to reduce data transfer sizes.
- Limit the number of simultaneous connections to avoid overloading your network.
- Monitor your bandwidth usage and adjust settings as needed.
By following these tips, you can ensure that your RemoteIoT solution performs at its best, even behind a firewall.
Conclusion: Wrapping It All Up
And there you have it – a comprehensive guide on how to use RemoteIoT behind a firewall on Windows. From understanding firewalls to configuring port forwarding and exploring third-party tools, we’ve covered everything you need to know to get started. Remember, setting up RemoteIoT behind a firewall requires a bit of patience and persistence, but the rewards are well worth it.
So, what are you waiting for? Grab a cup of coffee, roll up your sleeves, and start configuring your RemoteIoT setup today. And don’t forget to share your experiences in the comments below. We’d love to hear how it goes for you!
Oh, and one last thing – if you found this article helpful, be sure to check out our other guides on IoT and network security. Happy tinkering, and good luck